TLS Explained
Explore the basics of Transport Layer Security (TLS) and its importance in securing online communications. Learn how TLS protects data through encryption, the limitations of TLS 1.2, and the concept of perfect forward secrecy.
- published
- reading time
- 3 minutes
What is TLS?
Transport Layer Security (TLS) is a security protocol designed to protect communications over the internet. In the OSI model, it primarily resides in the Session Layer (Layer 5), though this classification can be nuanced.
Application Layer protocols like HTTP use TLS to secure communication.
How does HTTP look without TLS?
When establishing a connection between the client and the server:
- Syn: Client wants to establish a connection
- Syn-Ack: Server agrees to establish a connection
- Ack: Both are ready to communicate
The client sends a request to the server at port 80 (HTTP’s listening port), and the server responds with an HTML template.
What is the problem with HTTP?
All our requests pass through the ISP, which means that anyone with access (like the ISP) can snoop on your request packets and view the content. Therefore, HTTP communications are not private.
How can we secure communications?
Types of Encryption Algorithms
There are mainly two types of encryption algorithms:
- Symmetric: Faster and uses a single key for both encryption and decryption.
- Asymmetric: Slower and uses two different keys - public (for encryption) and private (for decryption).
Choosing Symmetric Key for Encrypting Data Over the Internet
Let’s say the client generates a symmetric key and encrypts the data with it. When the request is sent to the server, it is encrypted.
Question for Thought: How will the server decrypt the data?
Answer: The server needs the same key for decryption. So, when the client creates the connection, it sends the key to the server.
Problem: An attacker (like an ISP or a man-in-the-middle) could snoop on the request and capture the key, decrypting all communications.
Solution: Encrypt the key exchange using Asymmetric Key (PKI).
TLS 1.2
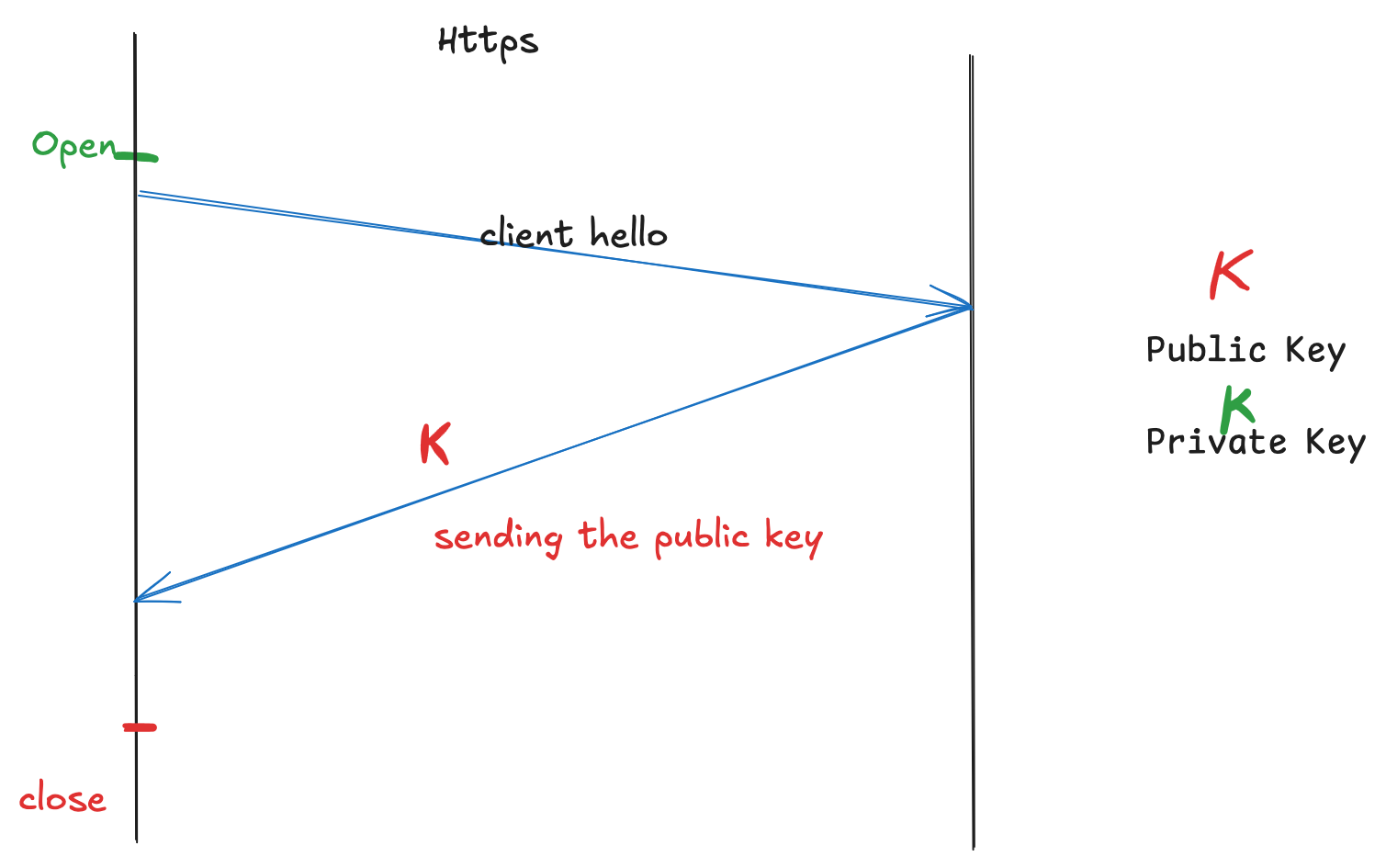
- The server has an RSA public key (for encryption) and a private key (for decryption).
- During the handshake, the server sends its public key to the client.
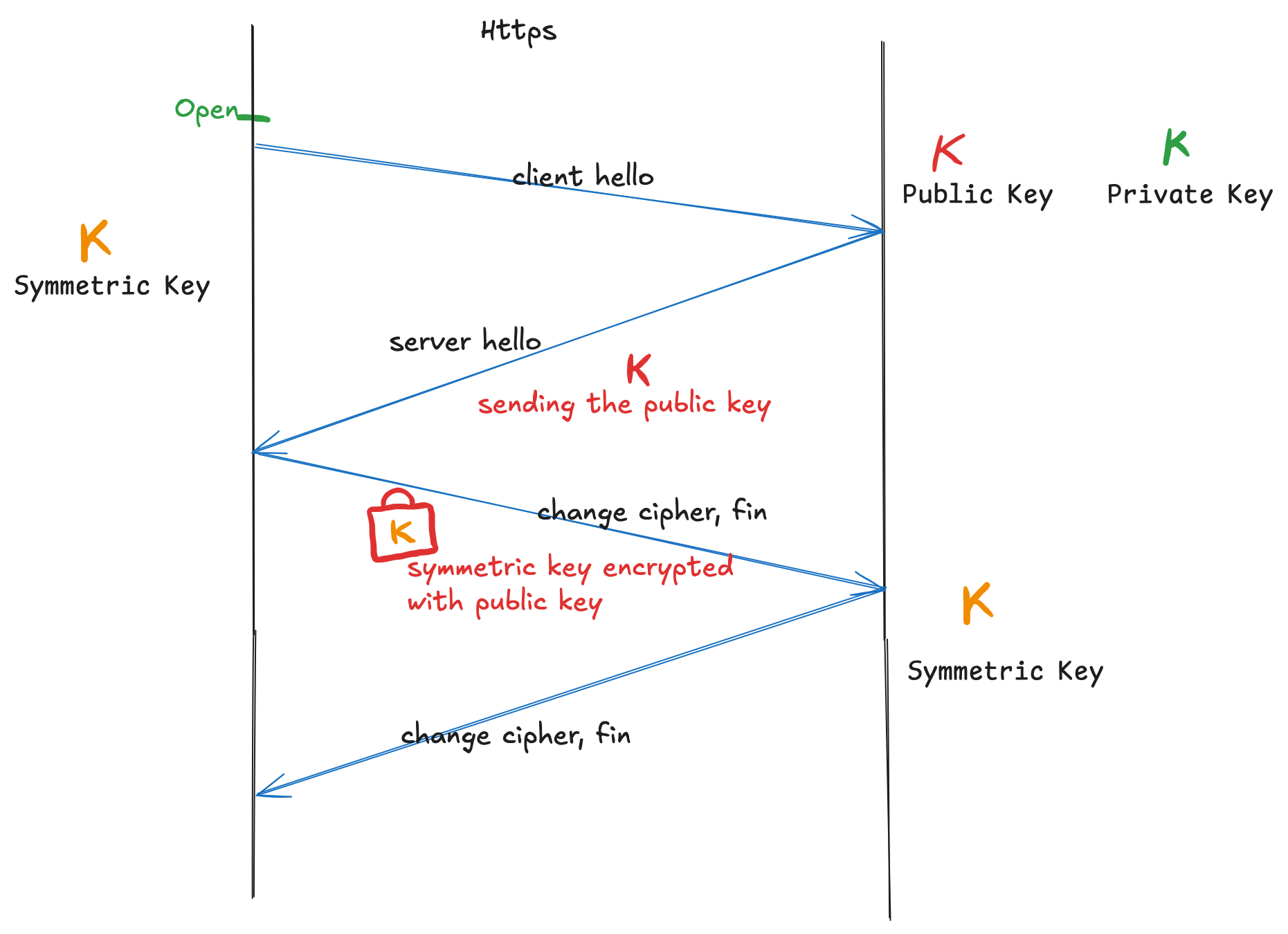
- The client generates a symmetric key, encrypts it with the server’s public key, and sends it to the server.
- Both the server and client now have the same symmetric key for encrypting and decrypting data during communications.
- All subsequent communications are encrypted with the symmetric key, ensuring security.
Good to Know
Perfect Forward Secrecy in TLS 1.2
TLS 1.2 is not foolproof as it does not provide perfect forward secrecy. If an attacker saves your communications and later obtains the server’s private key, they can decrypt past communications. This is why server certificates have expirations and why TLS 1.3 addresses this issue.
Leaking the private key is challenging but not impossible. For instance, the Heartbleed Bug in the OpenSSL library once allowed the server’s memory to be leaked, potentially exposing the private key.
Read more about it here: The HeartBleed Bug
